Sunday, September 25, 2011
New House For Rent Emerald Town House Bintaro Sektor 9
Added Jan 6, 2010, Under: Rumah
It is a 2 level home with :
- 3 bedrooms, 2 bathrooms.
- 1 bedroom and 1 bathroom for maid.
- Separate garage & carport can accommodate 1 or 2 cars.
- And a large garden (almost 1/3 of the total land).
Facilities :
- 2 new air conditioner with low voltages.
- Near to A Club House with a Swimming pool, Golf, Fitness center.
- A community park, gazebo & jogging track exclusively made for this cluster.
- Security card for entering cluster + 24 Hour guard.
- There are several International schools conveniently located near within the area.
Please contact 08129333630 for further Information available directly from owner.
- 3 bedrooms, 2 bathrooms.
- 1 bedroom and 1 bathroom for maid.
- Separate garage & carport can accommodate 1 or 2 cars.
- And a large garden (almost 1/3 of the total land).
Facilities :
- 2 new air conditioner with low voltages.
- Near to A Club House with a Swimming pool, Golf, Fitness center.
- A community park, gazebo & jogging track exclusively made for this cluster.
- Security card for entering cluster + 24 Hour guard.
- There are several International schools conveniently located near within the area.
Please contact 08129333630 for further Information available directly from owner.
By Unknown with 1 comment
Disewakan Rumah Maleo Bintaro sektor IX tanpa perantara
Added Jan 6, 2010, Under: Rumah
Rumah dua tingkat
3 kamar tidur
2 kamar Mandi
1 kamar pembantu + kamar mandi
Halaman belakang luas
Garasi untuk 2 mobil
Listrik 3500 watt
Lokasi asri dan nyaman
Untuk keterangan lebih lanjut hubungi no telepon 08129333630
By Unknown with No comments
Tuesday, April 5, 2011
Angklung A Traditional Music Instrument From Indonesia
Added Jan 6, 2010, Under: I Love Indonesia
Angklung is a musical instrument made out of two bamboo tubes attached to a bamboo frame. The tubes are carved so that they have a resonant pitch when struck. The two tubes are tuned to octaves. The base of the frame is held with one hand while the other hand shakes the instrument rapidly from side to side.
This causes a rapidly repeating note to sound. Thus each of three or more angklung performers in an ensemble will play just one note and together complete melodies are produced. Angklung is popular throughout Southeast Asia, but originated from Indonesia and it has been used and played by the Sundanese since the ancient times.
The word Angklung originated from two words angka and lung. Angka means "tone", and lung means "broken" or "lost". Angklung then means "incomplete tone".
In the Hindu period and the era of the Kingdom of Sunda, the angklung played an important role in ritual ceremonies such as ngaseuk pare, nginebkeun pare, ngampihkeun pare, seren taun, heleran, etc. These ceremonies were inherent to Sundanese communities; in courtly and everyday living.
In its function as the ritual medium, the angklung was played to honor Dewi Sri, the goddess of fertility, in a hope that their life and land will be blessed. Angklung is also used to signal time for prayer. Later, in Kingdom of Sunda these instruments were used as martial music in the Bubat War (Perang Bubat) as told in the Kidung Sunda.
The angklung functioned to build community spirit. Because of this, the playing of the angklung was forbade during the Dutch occupation of Indonesia. Because of this, the popularity of the instrument decreased and it came to be played only by children.
The oldest angklung still exist is called Angklung Gubrag. The angklung was made in the 17th century in Jasinga, Bogor. Nowadays, some of those older angklung remain in Sri Bduga Museum, Bandung.
As time flown by, the angklung received a more international attention. In 1938, Daeng Soetigna, from Bandung, created angklung that is based on the diatonic scale instead of the traditional pélog or sléndro scales. Since then, angklung has been used for educational and entertainment purposes and are able to accompany western music instruments in an orchestra.
One of the first well-known performances of angklung in an orchestra was during the Bandung Conference in 1955. Udjo Ngalagena, a student of Daeng Soetigna, opened his "Saung Angklung" (House of Angklung) in 1966 as a centre for its development.
UNESCO designated angklung as a Masterpiece of Oral and Intangible Heritage of Humanity on November 18, 2010. As part of the acknowledgment, UNESCO insisted that Indonesia preserve their heritage.
In Bali, an ensemble of angklung is called gamelan angklung (anklung). While the ensemble gets its name from the bamboo shakers, these days most compositions for Gamelan Angklung do not use them. An ensemble of mostly bronze metallophones is used instead, generally with about 20 musicians.
While the instrumentation of gamelan angklung is similar to gamelan gong kebyar, it has several critical differences. First, the instruments are tuned to a 5-tone slendro scale, though actually most ensembles use a four-tone mode of the five-tone scale played on instruments with four keys. An exception is the five-tone angklung from the north of Bali. But even in four-tone angklung groups, the flute players will occasionally touch on the fifth implied tone.
Secondly, whereas many of the instruments in gong kebyar span multiple octaves of its pentatonic scale, mosts gamelan angklung instruments only contain one octave, although some five-tone ensembles have roughly an octave and a half. The instruments are considerably smaller than those of the gong kebyar.
Gamelan angklung is often heard in Balinese temples, where it supplies musical accompaniment to temple anniversaries (odalan).
It is also characteristic of rituals related to death, and therefore connected in Balinese culture to the invisible spiritual realm and transitions from life to death and beyond. Because of its portability, gamelan angklung may be carried in processions while a funeral bier is carried from temporary burial in a cemetery to the cremation site. The musicians also often play music to accompany the cremation ceremony.
Thus many Balinese listeners associate angklung music with strong emotions evoking a combination of sacred sweetness and sadness.
The structure of the music is similar to gong kebyar, although employing a four tone scale. Jublag and jegog carry the basic melody, which is elaborated by gangsa, reyong, ceng-ceng, drum, and flute. A medium sized gong, called kempur, is generally used to punctuate a piece's major sections.
Most older compositions do not employ gong kebyar's more ostentatious virtuosity and showmanship. Recently many Balinese composers have created kebyar-style works for gamelan angklung or have rearranged kebyar melodies to fit the angklung's more restricted four tone scale. These new pieces often feature dance, so the gamelan angklung is augmented with more gongs and heavier gongs. Additionally, some modern composers have created experimental instrumental pieces for the gamelan angklung.
n the early 20th century, the angklung was adopted in Thailand, where it is called angkalung (อังกะลุง). The Thai angklung are typically tuned in the Thai tuning system of seven equidistant steps per octave, and each angklung has three bamboo tubes tuned in three separate octaves rather than two, as is typical in Indonesia.
Angklung has also been adopted by its Austronesian-speaking neighbors, in particular by Malaysia and the Philippines, where they are played as part of bamboo xylophone orchestras. Formally introduced into Malaysia sometime after the end of the Confrontation, angklung found immediate popularity.
They are generally played using a pentatonic scale similar to the Indonesian slendro, although in the Philippines, sets also come in the diatonic and minor scales used to perform various Spanish-influenced folk music in addition to native songs in pentatonic.
At least one Sundanese angklung buncis ensemble exists in the United States. Angklung Buncis Sukahejo is an ensemble at The Evergreen State College, and includes eighteen double rattles (nine tuned pairs) and four dog-dog drums.
By Unknown with 3 comments
IT Workers: Under Pressure and Underpaid
Added Jan 6, 2010, Under: O-News
Who couldn't use some good news these days? John Arnold, CIO at FedMed, a healthcare financial services organization in Rockville, Md., is ready for some. Four years ago, his IT staff was downsized from 14 employees to four, and they have experienced the familiar squeeze of salary freezes and increased workloads.The economy is strengthening, yet IT satisfaction is declining. Here's why IT workers are feeling the strain.
Since then, business has stabilized, and an acquisition last year injected new energy in the form of interesting projects, better benefits and the promise of new growth, Arnold says.
But he and his staff don't want to wait much longer for that energy to materialize into tangibles like raises and the go-ahead to hire more people.
So far, he says, camaraderie, loyalty and a strong sense of purpose, not to mention a dearth of employment opportunities, have kept the team together. "But if the company starts booming as a result of the acquisition and we don't see an adjustment in compensation, there will start to be some issues," Arnold says.
Many IT professionals share Arnold's frame of mind. And while there's reason to be hopeful, the skies still haven't completely cleared. Our survey shows that increases in total average compensation, salaries and bonuses are all higher this year than they were in 2010.
Respondents reported that total average compensation (including salary and bonus) is up 1.4%, whereas the increase reported in the 2010 survey was just 0.1%. Likewise, this year's survey shows an overall 1.5% salary increase and a 0.3% increase in bonuses, while the 2010 survey found a 0.7% increase in salaries and a 6.6% drop in bonuses.
These findings correlate with fall 2010 data from job search site Dice.com, which showed that IT salaries had increased slightly from the previous year, from $78,900 to $79,400.
Compared with last year's results, fewer of this year's respondents reported budget cuts, salary cuts or freezes, hiring freezes, permanent layoffs, training cuts or canceled projects. And fewer mentioned the economy as a challenge (28% this year, versus 31% last year).
But more than half of this year's respondents reported being "significantly affected" by budget cuts and heavier workloads, with 66% saying they expect continued workload increases in the next year.
Other findings indicate that IT professionals are growing impatient. Even with the uptick in pay, satisfaction with total compensation in relation to job responsibilities has decreased: In our 2010 survey, 55% of the respondents said they were "very satisfied" or "satisfied" in that regard, but the percentage of respondents choosing one of those answers fell to 50% this year.
In fact, 22% said they are less satisfied with their job now than they were a year ago, and 19% are less satisfied with their overall compensation. "The uncertainty with the healthcare situation is increasing employee contribution rates and out-of-pocket expenses," says a senior manager at a telecommunications giant.
Squeezed Dry
Consider the case of a director of technology at a small manufacturer in the South. He's the sole IT resource supporting about 60 users across six companies in five states, and he occasionally provides mechanical engineering support. "Like most in these lean times, my workload and what's expected of me has increased, though my salary has been flat for three years and bonuses were down to zero from about $6,000 the prior year, which was also down from the prior year," he says. Meanwhile, employees must contribute more to health insurance, and other benefits have been cut.Overall, 48% of the respondents reported that their base salary stayed the same or decreased from a year ago. Among those respondents, 62% said they've been affected by a salary freeze. It's no wonder then, that 40% reported feeling that they've plateaued financially over the past two years, and 33% said that they've lost ground. Only 27% reported gaining ground financially. Asked if they think they are paid fairly, more than half (52%) said they feel underpaid in light of their roles and responsibilities.
That may be due to the fact that 86% said that they have felt more pressure to increase productivity or take on new tasks. That can affect morale, even for those who consider themselves to be well paid -- especially if they've seen others get laid off. "As the layoffs continue, only those who can prove their worth can feel relatively safe," says a systems engineer at a U.S. telecom giant. That state of affairs has created a politicized atmosphere in which self-promotion is a survival tool. "It's a sign of tough times when you have to think about sacrificing your ethics not just to get ahead, but to simply survive," he says.
The systems engineer believes the situation may improve only when business picks up and management has to offer bonuses to keep people from leaving the company. "I believe those times for us may be on the horizon," he says.
Others agree that that type of pressure will help correct the balance of compensation and workload. Indeed, a senior manager at AT&T says management won't see the light until there is "a significant decrease in the experienced workforce" as a result of people retiring or moving on to new jobs at other companies.
He expects tensions to rise as people with flat salaries and increased workloads become aware of the discrepancy in total compensation between lower and upper management -- and see higher-value work go to contractors. And even with offers of higher pay, it may be difficult to entice employees who leave to come back as contractors, the senior manager says, because of "the stress and resentment currently being experienced by these workers in the current environment."
Tom Silver, Dice's senior vice president for North America, reports that about 40% of IT professionals say the way to earn more money is to move to another employer. That seems to indicate that people sense that the job market has more opportunities these days. Indeed, the No. 1 career concern among Dice survey respondents is no longer the possibility that their positions could be eliminated (just 15% chose that response, down from 25% last year); rather, it's the desire to find appropriate positions for their skill sets. "If people are no longer afraid of their position being eliminated, that gives them more confidence to move to another job," Silver says.
Some people switch jobs not for a pay increase but for security, better benefits or a less stressful business climate. For example, one CIO moved from a struggling bank to a smaller one that's profitable but pays 9% less and doesn't offer senior management bonuses. "Years ago, I just chased salary," he says. "But in the 'new economy,' I look for different attributes in a career."
By Mary Brandel
April 4, 2011 06:00 AM ET
By Unknown with No comments
Saturday, February 19, 2011
RAJA AMPAT ISLANDS WEST PAPUA ISLAND - INDONESIA
Added Jan 6, 2010, Under: I Love Indonesia
The Richest Marine Habitat in the World
The Raja Ampat, or “Four Kings,” archipelago encompasses more than 9.8 million acres of land and sea off the northwestern tip of Indonesia’s West Papua Province. Located in the Coral Triangle, the heart of the world’s coral reef biodiversity, the seas around Raja Ampat possibly hold the richest variety of species in the world.
The area’s massive coral colonies show that its reefs are resistant to threats like coral bleaching and disease —threats that now jeopardize the survival of corals around the world. In addition, Raja Ampat’s strong ocean currents sweep coral larvae across the Indian and Pacific Oceans to replenish other reef ecosystems. Raja Ampat’s coral diversity, resilience to threats, and ability to replenish reefs make it a global priority for marine protection.
Survey Confirms Highest Marine Biodiversity on Earth
In 2002, The Nature Conservancy and its partners conducted a scientific survey of the Raja Ampat Islands to collect information on its marine ecosystems, mangroves, and forests. The survey brought Raja Ampat’s total number of confirmed corals to 537 species— an incredible 75% of all known coral species. In addition, 899 fish species were recorded, raising the known total for Raja Ampat to an amazing 1,074. On land, the survey found lush forests, rare plants, limestone outcroppings, and nesting beaches for thousands of sea turtles.
Though human impacts here are less severe than elsewhere in Indonesia, Raja Ampat’s natural resources are endangered by over fishing and destructive fishing, turtle poaching, and unsustainable logging. The Indonesian government recently established Raja Ampat as a separate administrative unit, which will give communities a greater say in managing the natural resources upon which their livelihoods depend. This structure also offers an important opportunity to include conservation in the spatial planning of the newly formed local government.
Ensuring Conservation through Partnerships
To address these issues, the Conservancy launched a new project to protect Raja Ampat, working in close partnership with the government and communities to: 1) contribute to a comprehensive conservation action plan to protect Raja Ampat’s reefs and forests; 2) help incorporate marine protected area management into long-term planning and policy; and, 3) establish a network of marine protected areas for Raja Ampat.
The Conservancy’s ultimate goal is to protect Raja Ampat’s magnificent reefs while sustaining the livelihoods of local people. Raja Ampat includes the four large islands of Waigeo, Batanta, Salawati, and Misool, plus hundreds of smaller islands. The archipelago is part of an area known as the Bird’s Head functional seascape, which also contains Cenderawasih Bay, the largest marine national park in Indonesia.
By Unknown with 1 comment
Thursday, February 17, 2011
25 years of Windows Desktop
Added Jan 6, 2010, Under: Windows
Twenty-five years ago, on Nov. 20, 1985, Microsoft introduced its first version of Windows to the world. Not many people outside the technical press or the tech industry took notice. Product launch events that cost hundreds of millions of dollars were still years away.See how the world's most popular operating system has evolved over the last quarter century.
What's changed in Windows in the last 25 years? Plenty. In this image gallery, we take a look at the various faces of Windows over the past couple of decades and clue you in to what happened at every stage of the operating system's development.
1985: Windows 1.0
Windows started in 1981 as a project called Interface Manager and experienced a series of delays getting out of the gate. When it was finally released in late 1985 as Windows 1.0, it made a ripple, not a splash. It had to be run on top of DOS, few applications were written for it, and application windows couldn't be overlapped (they had to be tiled).
Still, the OS allowed for multitasking of Windows apps (not DOS ones) and, even though few knew it at the time, it would eventually become the foundation for the Microsoft empire.Windows 1.0 shipped with a handful of apps, including the Notepad text editor, a rudimentary calendar and the long-lived graphics painting program Paint. The operating system required MS-DOS Version 2.0, 256KB of memory and a graphics adapter. It could be run either from a hard disk or on two floppy disks running simultaneously -- in other words, you couldn't swap the disks in and out of a single drive.
1987: Windows 2.0
Windows 2.0 was released in the late fall of 1987, two years after the debut of Windows 1.0. New features in Version 2.0 included the ability to overlap application windows and improved memory use. Also new: Dynamic Data Exchange (DDE), which allowed Windows applications to automatically share and update data. For example, DDE allowed information in an Excel spreadsheet to be automatically updated when data in another Excel spreadsheet was changed.
Windows 2.0 also included expanded system requirements: It needed 512KB or more of memory and required DOS 3.0. A later version, Windows 2.11, would require the use of a hard disk for Windows for the first time.With Version 2.0, more applications written for Windows began to appear, including Microsoft Excel and Word. Aldus' PageMaker, originally written for the Mac, was also ported to Windows.
Windows 2.0 was notable for another reason as well -- on March 17, 1988, Apple Computer sued Microsoft, claiming that the look and feel of the Macintosh operating system was covered by copyright, and that Windows 2.0 violated that copyright. (Several years later, the case was resolved in Microsoft's favor.)
1990: Windows 3.0
Windows 3.0, released in 1990 -- and its successor, Windows 3.1, released in 1992 -- offered the first evidence that Windows might become the world's dominant desktop operating system. The interface was revamped, and although it looks awkward and kludgy today, at the time it was widely considered clean and sleek.
Icons were redesigned to use the VGA graphics standard with 16 colors. Memory handling was improved, and enhanced mode was added, which sped up memory access and allowed DOS programs to run in individual virtual machines. Windows 3.0 also allowed Windows applications to use more memory than was available in RAM by swapping RAM temporarily to the hard disk.Thanks to enhanced mode, DOS programs could be multitasked and run in their own resizable windows for the first time (previously, they had to run full-screen). Windows 3.0 required 640KB of what was called conventional memory and 256KB of extended memory. Version 3.00a of Windows was built to support multimedia, and it supported CD-ROMs for the first time.
Windows 3.0 also included what may be one of the greatest productivity-sappers in the history of computers -- the game of Solitaire.
Windows 3.1 introduced TrueType fonts, for better on-screen reading and higher-quality print output, as well as Object Linking and Embedding, which improved upon DDE for exchanging data between applications. Version 3.11 added support for networking using the dominant networking standard of the time, NetWare.
1993: Windows NT 3.1
Windows NT 3.1, released in July 1993, was built for businesses rather than consumers and was designed to be more secure and stable. It used a 32-bit rather than a 16-bit architecture. Version 3.1 was the first release of the NT operating system; earlier version numbers were skipped so that the numbering for this business OS would match that of the consumer OS, Windows 3.1. NT required an 80386 CPU, 12MB of RAM (16MB was recommended) and 90MB of free hard disk space.
The enterprise-oriented operating system went through three more releases -- Windows NT 3.5 in 1994, Windows NT 3.51 in 1995 and Windows NT 4.0 in 1996 -- before moving to Microsoft's year-based version numbering convention with Windows 2000.1995: Windows 95
Windows 95, released in August 1995, combined DOS with Windows for the first time: Rather than installing Windows on top of DOS, you installed only Windows 95, which included both DOS and Windows. It was also the first consumer version of Windows that began moving away from a 16-bit architecture and toward a 32-bit one; in other words, it was a mix of 32-bit code and 16-bit code.
The operating system introduced many interface improvements, including several that live to this day, such as the taskbar and the Start menu. Support for file names longer than eight characters was added as well. It was far more stable than previous versions of Windows and was the first to support Intel's Plug and Play standard, which was designed to make it easier to add hardware and peripherals to your PC; the idea was that Windows would automatically recognize and configure attached hardware. It was a step forward, but it didn't always work -- some people referred to it as "plug and pray."
At a minimum, Windows 95 required an 80386 DX CPU, 4MB of system RAM and 120MB of hard drive space -- although it was sluggish on a computer that just met those requirements. An 80486-based PC and 8MB of RAM made for a much better experience.
Windows 95 was notable for another reason as well -- the massive marketing campaign that accompanied its launch was said to have cost $300 million and included purchasing the rights to the Rolling Stones song "Start Me Up" as the Windows 95 theme song; draping a 300-foot Windows 95 banner over Toronto's CN Tower; lighting the Empire State Building with Microsoft's corporate colors of yellow, red and green; and creating a promotional instructional video that featured Jennifer Aniston and Matthew Perry from the hit TV show Friends.
1998: Windows 98
Windows 98, released in June 1998, was as not as big a step forward over Windows 95 as Windows 95 had been over Windows 3.1. Rather, it made incremental changes to Windows, although there were a few significant additions.
The most notable had to do with Internet support. For the first time, the Winsock specification -- which provides TCP/IP support for Windows -- was built directly into the operating system, rather than having to be installed as an add-on. Also for the first time, Internet Explorer was included as part of the operating system, which eventually led to the U.S. Justice Department's prosecution of Microsoft for antitrust violations.Windows 98 offered considerably better USB support than Windows 95 did. A feature called Active Desktop was supposed to deliver live Internet content to the desktop, but it proved to be buggy and was dropped from subsequent versions of Windows.
Windows 98 required at least a 66-MHz 486DX2 processor, 16MB of RAM (24MB was recommended) and 500MB of hard disk space.
2000: Windows 2000
Windows 2000, the successor to Windows NT 4.0, released in February 2000, was intended for business rather than home use, and it was available in several editions, including multiple server versions. It brought many features of Windows 98 into the NT line, including Internet Explorer and Plug and Play. Windows File Protection, which protected important system files, was introduced along with the Encrypting File System, which improved security by encrypting files automatically, and Active Directory, the enterprise technology used to provide network and domain services.
System requirements for Windows 2000 varied depending on whether the server or desktop version, called Windows 2000 Professional, was being installed. Windows 2000 Professional required at least a 133-MHz Pentium microprocessor (or the equivalent), 32MB of RAM (64MB was recommended) and a 2GB hard disk with 650MB of free space.2000: Windows Me
Windows Me (also called Windows Millennium Edition) was released in September 2000 and quickly became one of Microsoft's most criticized operating systems because of installation problems, bugs and hardware and software incompatibilities. It introduced Windows Movie Maker. Critics maintain that it was introduced only for marketing purposes, to give Microsoft something to sell for the 2000 holiday season.
Windows Me was the last version of Windows that included the DOS architecture. It lasted little more than a year, until Windows XP was introduced. Windows Me required a 150-MHz Pentium processor or the equivalent (a 300-MHz model was recommended), 32MB of RAM (64MB was recommended) and 320MB of free hard drive space (2GB was recommended).
2001: Windows XP
Windows XP, released in August 2001, was a breakthrough in several respects. It was the first version of Windows that did not use DOS as part of its underlying architecture, and the first to be offered in both 64-bit and 32-bit editions. XP combined the desktop version of the secure and stable enterprise-oriented Windows NT/2000 line with the consumer-focused Windows line. (The Windows Server OS line has continued separately from the desktop line.)
It was far more stable than previous versions of Windows and featured a significantly revamped interface that was brighter, more colorful and more contemporary-looking. Drop shadows were added to icon labels, windows were given a more rounded look and visual effects such as fading and sliding menus were added. Windows XP introduced a slew of new features, including background themes and remote desktop, which allows a PC to be controlled remotely via the Internet or a network.
Windows XP shipped in multiple versions, most notably Windows XP Home Edition and Windows XP Professional. Even though it was introduced nine years ago, XP remains the most-used version of Windows, and it's still available as a downgrade option on new PCs that run the Windows 7 Professional or Ultimate editions. Windows XP requires a Pentium 233-MHz processor or the equivalent (a 300-MHz model is recommended), at least 64MB of RAM (128MB is recommended) and at least 1.5GB of available space on the hard disk.2006: Windows Vista
Windows Vista, released at end of 2006, may well be the most criticized and disliked version of Windows of all time. Released more than five years after Windows XP, Vista faced widespread hardware incompatibilities upon launch and wouldn't run on older hardware.Vista's interface was significantly different from XP's interface. Most notably, it had a new feature called Windows Aero, a set of visual enhancements that included transparent windows and animations. There were also a variety of other new features, including the Windows Sidebar, Desktop Gadgets, the Windows Photo Gallery and improved search. Some people disliked Vista's resource-hungry user interface, and those who did like it couldn't always get it: Many PCs that were sold as "Vista-capable" couldn't run the full version of Vista, leading to a class-action lawsuit against Microsoft.
Windows Vista was available in six different versions. Most PCs were sold with Windows Vista Home Premium. It required a 1-GHz processor (either 32- or 64-bit), 1GB of system memory, 15GB of free hard disk space and a graphics card that was able to support Windows Aero.
2009: Windows 7
Windows 7, released in October 2009, is Microsoft's current desktop operating system. Many people feel it's the OS that Windows Vista should have been. It retains the Aero interface and other enhancements from Vista, but rather than adding a slew of new features in Windows 7, Microsoft focused more on fixing the shortcomings of Vista. Windows 7 is generally considered more stable than Vista, and most users upgrading from Vista to Windows 7 did not experience the kinds of hardware problems that they encountered when they upgraded from XP to Vista.
Windows 7 did introduce a few new features -- notably an enhanced taskbar, a slightly redesigned Start menu and a trio of nifty navigation shortcuts known as Aero Peek, Aero Snap and Aero Shake. Some features of Windows Vista were taken away, including the Windows Photo Gallery and Windows Mail.Windows 7 comes in multiple versions, including Windows 7 Home Premium, Windows 7 Professional and Windows 7 Ultimate. It requires a 1-GHz processor (either 32- or 64-bit), 1GB of system memory, 16GB of free hard disk space (20GB for the 64-bit version) and a graphics card that's able to support Windows Aero.
What's next?
No one, including Microsoft, knows the shape that Windows will take in the next 25 years, because there's simply no way to peer that deeply into the technology future. It's a good bet, though, that the Windows of 25 years from now will be radically different from today's version.In fact, it's reasonable to expect that there will be greater changes to Windows in the next 25 years than in its first 25 years. That's the case because, despite all the changes in technology, for the past several decades the personal computer, whether desktop or laptop, has been people's main computing device. It's not clear that that will be true in the next 25 years, given the prevalence of smartphones and the increasing popularity of tablets.
Several questions spring to mind: How will Windows accommodate the increasing role of cloud-based software and services in computing? Will operating systems even matter in the future? Will Windows move to a modular model, with pick-and-choose components?
For now, Microsoft isn't saying. In the meantime, we'll have our first peek at the future of Windows when the first Windows 8 beta is released sometime next year.
Want more Microsoft history? See Microsoft turns 35: Best, worst and most notable moments
.
Preston Gralla is the author of more than 35 books, including How the Internet Works, Windows XP Hacks, and Windows Vista in a Nutshell.
By Unknown with No comments
Tuesday, February 15, 2011
Phinisi from Bugis
Added Jan 6, 2010, Under: I Love Indonesia
Phinisi merupakan kapal layar tradisional Suku Bugis dan Suku Makassar di Sulawesi Selatan. Pinisi adalah sebuah kapal layar yang menggunakan jenis layar sekunar dengan dua tiang dengan tujuh helai layar yang mempunyai makna bahwa nenek moyang bangsa Indonesia mampu mengharungi tujuh samudera besar di dunia. Kapal Phinisi umumnya memiliki dua tiang layar utama dan tujuh buah layar, yaitu tiga di ujung depan, dua di depan, dan dua di belakang; umumnya digunakan untuk pengangkutan barang antarpulau. Diperkirakan kapal pinisi sudah ada sebelum tahun 1500an. Menurut naskah Lontarak I Babad La Lagaligo pada abad ke 14, Pinisi pertama sekali dibuat oleh Sawerigading, Putera Mahkota Kerajaan Luwu untuk berlayar menuju negeri Tiongkok hendak meminang Putri Tiongkok yang bernama We Cudai.
Dalam proses pembuatan Kapal Phinisi, para pengrajin pembuat kapal harus menghitung hari baik untuk memulai pencarian kayu sebagai bahan baku. Biasanya jatuh pada hari ke lima dan ke tujuh pada bulan yang berjalan. Angka 5 (naparilimai dalle'na) yang artinya rezeki sudah di tangan. Sedangkan angka 7 (natujuangngi dalle'na) berarti selalu dapat rezeki. Setelah dapat hari baik, lalu kepala tukang yang disebut "punggawa" memimpin pencarian kayu. Untuk jaman sekarang, kayu dicari dengan membeli kepada tukang penjual kayu.
Setelah kayu didapat, proses peletakan lunas (kayu dasar) kapal dimulai, dengan meletakkan lunas menghadap Timur Laut. Balok lunas bagian depan merupakan simbol lelaki. Sedang balok lunas bagian belakang diartikan sebagai simbol wanita. Usai dimantrai, bagian yang akan dipotong ditandai dengan pahat. Pemotongan yang dilakukan dengan gergaji harus dilakukan sekaligus tanpa boleh berhenti. Itu sebabnya untuk melakukan pemotongan harus dikerjakan oleh orang yang bertenaga kuat. Demikian selanjutnya setiap tahapan selalu melalui ritual tertentu.
Ada 4 suku besar yang memiliki keahlian dan tradisi terhadap Kapal Phinisi (pinisi) ini yaitu :
Ada dua jenis kapal pinisi
Kapal Phinisi dibangun dengan cara tradisional yang seksama dengan menggunakan kayu pilihan yaitu Kayu Besi/Kayu Ullin/Ulin/Ironwood (Eusideroxylon zwageri) dan Bangkirai atau Shorea spp. (mis. Shorea kunstleri King, Shorea laevis Ridley, Shorea laevifolia Endert) atau Hopea spp. (mis. Hopea celebica Burck, Hopea semicuneata Sym.). Kayu Bangkirai yang sering digunakan adalah dari jenis shorea leavifolia.
Nama umum Shorea laevifolia
Indonesia: Bangkirai, benuas, anggelam
Klasifikasi Ilmiah :
Kingdom: Plantae (Tumbuhan)
Subkingdom: Tracheobionta (Tumbuhan berpembuluh)
Super Divisi: Spermatophyta (Menghasilkan biji)
Divisi: Magnoliophyta (Tumbuhan berbunga)
Kelas: Magnoliopsida (berkeping dua / dikotil)
Sub Kelas: Dilleniidae
Ordo: Theales
Famili: Dipterocarpaceae
Genus: Shorea
Spesies: Shorea laevifolia Endert
Kerabat Dekat
Tengkawang, Tengkawang, Tengkawang Layar, Damar, Damar Mata Kucing, Tengkawang, Tengkawang Tungkul, Tengkawang, Tengkawang Layar, Damar Tanduk, Tengkawang, Tengkawang, Tengkawang Majau, Tengkawang, Tengkawang Terendak, Tengkawang, Gisok, Tengkawang, Tengkawang, Belangeran, Meranti Tembaga, Damar Pakit, Belangiran, Damar Kedontang, Damar Siput, Damar Buah, Damar Tenang, Balau Merah, Damar Tunam, Banio, Damar Munsarai, Damar Mesegar, Damar Maja.
Dalam proses pembuatan Kapal Phinisi, para pengrajin pembuat kapal harus menghitung hari baik untuk memulai pencarian kayu sebagai bahan baku. Biasanya jatuh pada hari ke lima dan ke tujuh pada bulan yang berjalan. Angka 5 (naparilimai dalle'na) yang artinya rezeki sudah di tangan. Sedangkan angka 7 (natujuangngi dalle'na) berarti selalu dapat rezeki. Setelah dapat hari baik, lalu kepala tukang yang disebut "punggawa" memimpin pencarian kayu. Untuk jaman sekarang, kayu dicari dengan membeli kepada tukang penjual kayu.
Setelah kayu didapat, proses peletakan lunas (kayu dasar) kapal dimulai, dengan meletakkan lunas menghadap Timur Laut. Balok lunas bagian depan merupakan simbol lelaki. Sedang balok lunas bagian belakang diartikan sebagai simbol wanita. Usai dimantrai, bagian yang akan dipotong ditandai dengan pahat. Pemotongan yang dilakukan dengan gergaji harus dilakukan sekaligus tanpa boleh berhenti. Itu sebabnya untuk melakukan pemotongan harus dikerjakan oleh orang yang bertenaga kuat. Demikian selanjutnya setiap tahapan selalu melalui ritual tertentu.
Ada 4 suku besar yang memiliki keahlian dan tradisi terhadap Kapal Phinisi (pinisi) ini yaitu :
- Suku Konjo disekitar daerah Ara, Bira, and Tanah Biru
- Suku Mandar disekitar daerah Sulawesi Barat dan Utara
- Suku Bugis (Bougies) disekitar daerah Wajo dan Teluk Bone
- Suku Makasar (Makassarese) disekitar daerah Makassar
Ada dua jenis kapal pinisi
- Lamba atau lambo adalah Pinisi modern yang masih bertahan sampai saat ini dan sekarang dilengkapi dengan motor diesel (PLM) atau Kapal Layar Motor (KLM) atau "Motor Driven Sailing Vessel" atau "Motor Sailor." Penggunaan mesin (diesel/vessel) terjadi sekitar tahun 1970-an ketika kecepatan kapal perlu ditingkatkan dan ketepatan waktu dalam pengantaran barang ke seluruh Indonesia.
- Palari adalah bentuk awal pinisi dengan lunas yang melengkung dan ukurannya lebih kecil dari jenis Lamda.
Kapal Phinisi dibangun dengan cara tradisional yang seksama dengan menggunakan kayu pilihan yaitu Kayu Besi/Kayu Ullin/Ulin/Ironwood (Eusideroxylon zwageri) dan Bangkirai atau Shorea spp. (mis. Shorea kunstleri King, Shorea laevis Ridley, Shorea laevifolia Endert) atau Hopea spp. (mis. Hopea celebica Burck, Hopea semicuneata Sym.). Kayu Bangkirai yang sering digunakan adalah dari jenis shorea leavifolia.
Nama umum Shorea laevifolia
Indonesia: Bangkirai, benuas, anggelam
Klasifikasi Ilmiah :
Kingdom: Plantae (Tumbuhan)
Subkingdom: Tracheobionta (Tumbuhan berpembuluh)
Super Divisi: Spermatophyta (Menghasilkan biji)
Divisi: Magnoliophyta (Tumbuhan berbunga)
Kelas: Magnoliopsida (berkeping dua / dikotil)
Sub Kelas: Dilleniidae
Ordo: Theales
Famili: Dipterocarpaceae
Genus: Shorea
Spesies: Shorea laevifolia Endert
Kerabat Dekat
Tengkawang, Tengkawang, Tengkawang Layar, Damar, Damar Mata Kucing, Tengkawang, Tengkawang Tungkul, Tengkawang, Tengkawang Layar, Damar Tanduk, Tengkawang, Tengkawang, Tengkawang Majau, Tengkawang, Tengkawang Terendak, Tengkawang, Gisok, Tengkawang, Tengkawang, Belangeran, Meranti Tembaga, Damar Pakit, Belangiran, Damar Kedontang, Damar Siput, Damar Buah, Damar Tenang, Balau Merah, Damar Tunam, Banio, Damar Munsarai, Damar Mesegar, Damar Maja.
By Unknown with 1 comment
10 Simple Marketing Strategies to Promoto Your Blog
Added Jan 6, 2010, Under: O-News
If you run an online business, blog or website you know you need to be marketing. Maybe you aren’t sure where to start.These ten tips are things you can start implementing right away to grow your business and start getting the word out about your product or service. These tips should be used over and over to continually grow awareness of your blog/product or service. Use them weekly, but they are easy enough that you can start using them today.
1. Interact on related blogs & forums.
Simply find blogs and forums that are in the same niche or category as your site and start interacting with people. You can leave comments, offer helpful advice and suggestions or just get to know people.
2. Write and distribute to article directories.
Writing an informative article is something you can do today. There are many article directories that will allow you to post your article for free. Not only is this a way to give readers pertinent information but you also get a backlink in your bio or resource box.
3. Guest blog.
You may not get a guest blogging spot today, but you can write the blog post and start contacting blog owners to see if they are interested.
4. Create a compelling email signature.
You need to do this in your autoresponder signature as well as your personal email signature.
5. Create videos and put on Youtube.
Videos are getting more popular every day. You can create several short videos, upload them to Youtube and then share the links with your readers, in your email signature, on Twitter and Facebook. Don’t like seeing yourself on screen? That’s not a problem, you can create Power Point Presentations for the visual and then read from a script so all that’s “seen” of you is your voice.
6. Write a review.
You can write reviews on products you’ve tried, ebooks you’ve read, webinars, videos, books you’ve read, affiliate programs. The list is endless on things you can review to help your readers and give you exposure.
7. Tweet to your followers.
You don’t have to get on Twitter every single day and bombard your followers with tweets, but you can use Twitter as a strategic source to build your following, set up your personal brand and reach out to others looking for your information.
8. Share your stuff on Facebook.
You can set your blogs to post on Facebook through Networked Blogs, you can set up plugins that allow you and others to share your blog posts on social networks. Utitilize these tools for yourself too. Your readers aren’t the only ones who can use them–you can too.
9. Email your list.
This one is pretty self explanatory, you can email your list once or twice a week with updates, promotions and other stuff. If you don’t have a list, start a list building campaign and start sending people to your opt-in page.
10. Create a free report.
You can write up a report to give away that contains relevant information to your website, product or service. Brand it with your website address in the footer so people know where to go to find more information.
These are all pretty simple methods you can start doing immediately to grow traffic to your blog or website. Do you have any simple solutions not mentioned here that you’d like to share? We’d love to hear from you.
Written by Patti Stafford
By Unknown with No comments
Sunday, February 13, 2011
Phinisi Sailing Boats are made from Sulawesi island, Indonesia
Added Jan 6, 2010, Under: I Love Indonesia , O-News

Now let’s flashback to the early history of phinisi boat at the southern tip of Sulawesi island, where local community build a maritime tradition for hundreds of years. The stories about the courage of the sailors of Bugis, Makassar, Mandar, and Konjo has become a byword to a distant country across the ocean. The beauty and resilience in the face of malignancy boat sea waves, has produced stories of heroism are admirable.
The story of the boat from Tanah Beru Phinisi and the sailors from the Bira, Bulukumba, who drove the boat, now is not an ordinary story. But not many realize the greatness of the sailors from the southern tip of Sulawesi, was built from a long tradition. This culture is based on the myth of the creation of the first boat by their ancestors.
Once Upon A Time in the mythology of Tanah Beru community, their ancestors create a larger boat for sailing on the sea, carrying merchandise and catch fish. When the first boat made, it’s been voyaged at sea. But accidents happen on the road. Waves and storm struck the boat and destroy it. Body parts dumped in the village of Ara boats, sailing and landed at Cape Bira landed in the Land of Lemo.This incident seems to be a symbolic message to the village of Ara. They must beat the sea with their cooperation. Since the incident, Ara only as a special boat manufacturer. People who acquire the remaining special sailboat pleased to learn about astrology and the signs of nature. Lemo-Lemo While people are entrepreneurs who invested and used boats. The tradition of segregation of duties has been going on for years which finally led to the creation of a traditional wooden boat called Phinisi.
Now the mystical belief of the ancient mythology is still strong in every process of making Phinisi. Starting with a small ritual, boats Phinisi made after cutting ceremony in full. The ceremony was led by a boat handler called Panrita Lopi.Various bidding requirements that they are not allowed to get behind in this ceremony as all snacks should taste sweet and healthy white chickens. Cake to generate the wishes of the owner of the boat will carry a higher profit. A little blood from white chickens attached to the boat hull. Ritual as a symbol of hope that there is blood spilled in the ship being designed. Then, his head cut off both ends of the hull builder and submit it to the boat-making leader. The tip pieces settled to the sea front in the exhaust as a sign that the ship can be fused with the waves at sea. Being back in pieces thrown to the ground as far as boats go to sea reminded that he must return him safely to shore. In the end, proclaiming Lopi Panrita prayers before the Creator.
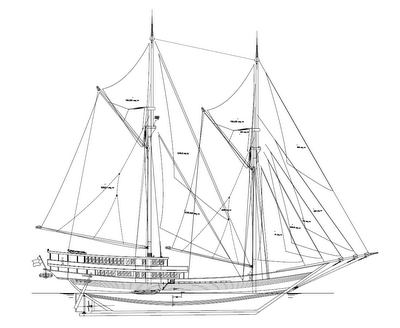
1. Anjong, triangle in front of as an imbalance.
2. Sombala, main screen large reach 200 m.
3. Tanpasere, triangular small screen in every major pillar.
4. Cocoro pantara, auxiliary screen in front
5. Cocoro tangnga, maid was in the middle of the screen.
6. Tarengke, auxiliary screen behind.
Related to this story phinisi ship, not afraid of the people in Bulukumba, South Sulawesi, that phinisi ship design will be submitted by foreign patents. Given the manufacturing center of the boat or ship phinisi the largest in the world located outside Indonesia. Examples of centers that exist only in some countries such as Japan, Australia, Malaysia and Brunei. Previously, the ship was already well known as a producer Bulukumba phinisi first with the best quality.
PHINISI BUILDER AT TANAH BERU
This a place are famous phinisi boat, the phinisi boat called Phinisi Nusantara had sailed crossing the pacific ocean to Vancouver, Canada, Ammanagappa sailed until Madagaskar, Hati Marege sailed the ocean of south of east Timor until Darwin, Australia and Damar Sagara sailed to Philippine-Japan-Africa.Bonto Bahari people combined their technical skill and magic to build the boat. People of area and Lemo – Lemo are expert of making phinisi boat but are not good sailors. People of Bira are expert in sailing but they don’t have skill to build phinisi. In this pleace you will feel amazing to watch people of Bonto Bahari skill building a phinisi with traditional tools. Each phinisi building holds a traditional ceremony.
By Unknown with No comments
Sunday, February 6, 2011
Free Open-Source Tools for Network Admins
By High Mobley
February 2, 2011 06:11 AM ET
PHP Weathermap does not handle its own data collection, so you'll need to pair it with another application such as Cacti, OpenNMS, MRTG, or RRDtool. PHP Weathermap has a plug-in that helps it integrate into Cacti, with some options available in the Cacti preference panels.
You will need to edit the map config files to adjust the appearance of your maps. You can do this by hand, though PHP Weathermap offers a GUI editor that runs within a Web browser. You can use the editor to create your nodes (routers and switches) and links, as well as produce a functioning map.
When you're ready for manual tweaking, you can add custom background images to the map and insert custom icons for your routers. You can also add subnodes, which allow you to display more information within the router's icon, such as CPU or memory usage. You can also insert parallel links or bonded links between routers.
Through further tweaking of config files, you can fine-tune the placement of router icons and the map's legend. If you have a more complicated map with plenty of router icons, you can create curved link lines between your router icons to help keep the map readable and less cluttered or cramped.
Top free open source tools for network admins: NtopNeed an sFlow or NetFlow collector to get a thorough look at your data traffic flows? Ntop will take NetFlow or sFlow data from popular switches and routers and display it in a Web GUI, complete with clickable links that take you to details about particular hosts or protocols or to actual conversations and flows.
There are interesting features to Ntop's output, such as identifying workstation users by their email addresses and (passively) detecting the operating systems of network hosts through packet analysis. Ntop will break down traffic volume on a per-protocol basis, helpful for comparing the traffic your network actually has to what you think it should have.
Ntop can give you a list of IP protocols, sortable by protocol type, as well as lists of traffic sources and destinations. Ntop also creates a matrix table of IP traffic, so you can see who is talking to whom and how much data is being passed between the two. Of course, data is not as useful if you cannot sort it. Ntop allows you to sort on both the traffic source and the destination.
Platforms supported include Windows and all major Unix types, such as Linux, the BSDs, Solaris, and Mac OS X. Although resource usage will vary by network size and the configuration options that you choose, Ntop should be very light on modern workstation and laptop hardware. Ntop's Web UI accepts multiple HTTP usernames and passwords, so each member of your NOC team can have individual access, and you can force Ntop to work with HTTPS.
Ntop supports a wide range of network protocol types, IP protocol types, and even network media types. There is support for several VoIP protocols, including Cisco SCCP, Asterisk's IAX protocol, and of course SIP. Ntop can even do protocol decodes on most common IP protocols. If you want the information for later retrieval and analysis, Ntop can record its network traffic data to RRD-style files on a disk.
February 2, 2011 06:11 AM ET
Routing issues, slow network applications, DNS resolution problems -- a network administrator has to deal with a host of network nuisances on a daily basis. How do you survive when you're constantly under the gun to fix the problems? Like any other professional, you need a solid set of tools.
Not surprisingly, plenty of options exist in the open source camp. Excellent open source software tools are available to help you keep a close watch over your network, as well as meet many other needs of the busy network manager. From monitoring, troubleshooting, and security analysis tools to utilities for keeping track of IP allocations, passwords, and router configurations, here are my top 10 picks of the most essential open source tools for our network admin toolbox -- all free for the downloading.
This is by no means an exhaustive list of open source networking utilities available, and I've merely touched on their capabilities. Are there other free open source tools that you use regularly but we didn't list here? Leave a comment and let us know!
At the heart of it, Dig is a command-line utility that performs DNS queries. That alone is helpful, but Dig can also tell you most everything about the queries and replies -- you'll sometimes need that extra information to determine why you're getting a strange reply from a DNS server. The default output of Dig provides you with all the data you'll require for troubleshooting: reply/error codes from the server, flags used in the query, a reiteration of your query, the answer to your query, how long the query took, which server it received the reply from, and how much data it received in the reply. Dig can be quite useful when you're trying to diagnose slow network applications, by determining how long it takes a computer to get DNS resolution for the application server's domain name.
Dig can ask for a typical name query, replying with an IP address when you give it a domain name. You can also do a reverse lookup: By using the -x switch and giving it an IP address, Dig it will return the corresponding domain name for that IP address. The -t switch lets you specify the type of query you're making, so you can ask for mail server records (MX), name server records (NS), text records (TXT), and more.
If you are sporadically getting incorrect replies to your DNS queries, it's possible that one of your DNS servers has a different set of DNS records than the others. With Dig, you can run the same query against each of your DNS servers to find out which one is providing the erroneous replies. Just give Dig the DNS server's address with the @ symbol in front:
dig @4.2.2.2 www.yourdomain.com
Are you troubleshooting DNS problems with servers that use transaction signatures? Dig lets you specify a TSIG key to use for your queries. Dig also lets you tailor IPv6-only queries to help you troubleshoot IPv6-specific problems.
Dig is a part of the client utilities of the BIND project. It is not generally installed by default, but is readily available on all Unix, Linux, and BSD variants, including Mac OS X. A Windows version is available too.
Nmap is a lightweight security scanner that's heavy on utility. Nmap can perform tasks as simple as a ping sweep to see which IP addresses are active and responding, as well as carry off complex scripts to scan your systems for known vulnerabilities. Another fun feature of Nmap is the ability to analyze the reply packets it receives from a host to determine which OS the host is running.
Nmap is most commonly used to see which services or ports are open or available on a host. It supports both TCP and UDP scanning. You can give it a single host to scan or a CIDR (Classless Inter-Domain Routing) block or an entire list of hosts and networks from a file. A dizzying range of options allows you to specify which types of packets to send out and to see which hosts are susceptible to various remote attacks. Additionally, Nmap provides several options to bypass firewalls and other network filters that would otherwise block your scans.
Nmap also includes the Nmap Scripting Engine (NSE), which combines custom scripts with existing Nmap functionality to perform more specific discovery and attack analyses than Nmap does by itself. Fyodor and David Fifield gave an excellent talk and demonstration on the NSE at the Black Hat conference in Las Vegas last year. In the demonstration, Fyodor showed the results of Nmap scans against Microsoft company computers that used some of the NSE's MS RPC discovery scripts. The scripts used rpcinfo to gather info such as share names and usernames from the Windows computers. There are 177 NSE scripts available from Nmap.org as of this writing, and because they are user contributed, the list of NSE scripts is expanding at an amazing pace.
If you're a longtime user of Nmap but haven't kept up with Nmap news and releases, you'll want to check out the Zenmap GUI's new network topology feature, which lets you create an interactive network map based on information gathered by Nmap. The map begins with localhost at the center and displays all discovered hosts in concentric rings around it, the rings indicating the number of hops away the hosts are. From there you can shift the focus to another host or get more info by clicking a host's icon in the map. The shape of the icon refers to the type of device, and the size indicates the number of open ports.
All this makes Nmap perfect for checking on IP address usage, scanning for security vulnerabilities, and ensuring your firewalls and routers are operating properly.
Enter KeePass, an encrypted database program to store all of your usernames, passwords, access URLs, and more. You can restrict access to the KeePass database with a password, a key file, or both. The password database is encrypted with either AES or the Twofish encryption algorithm, and not as one contiguous file but in 256-bit chunks -- decrypting a single piece of data nets a cracker little or no useful data. Plus KeePass encrypts all the data in its database, not just the passwords, so your usernames, URLs, and other notes are safe as well.
You can create groups for password records to help organize the info if you have a lot of passwords to track. Groups can have subgroups, subgroups can have subgroups, and so on. A search function helps you quickly find the password record you need.
How do you share the KeePass database with coworkers who are running Mac OS X or some other version of Unix? No problem. KeePass is ported to Windows, Mac OS X, various Linuxes, and popular mobile phone platforms, including iPhone, Android, and BlackBerry. Because the KeePass database is stored in a single file, it's easy to distribute among your NOC team. Did I mention that KeePass is portable, needing no installation on Windows or Mac OS X? You can carry it with you on a USB stick or download it to a computer without leaving any unwanted registry entries or library files.
Already using another password manager? KeePass can import your existing password database in formats from a variety of programs such as Password Keeper, CodeWalletPro, and Password Agent. Other file formats are supported through KeePass plug-ins.
IPplan is not a generic spreadsheet or database application. It is tailored to tracking IP addresses, so it understands and enforces CIDR blocks. Each address record has support for contact info, hardware, DNS name, location, description, MAC address, NAT address tracking, and a generic "additional information" field. You can also upload a file to attach to the IP address record.
IP address records are organized into subnets (CIDR blocks), which are assigned to customers or autonomous systems. Subnets are further organized into network areas or ranges (supernets) within the customer hierarchy. Because IPplan is designed for use by ISPs, it works well for organizing enterprise addresses for companies with multiple locations and complex networks that use multiple AS (Autonomous System) numbers. If you decide to rework the subnets on your network, no problem. IPplan handles changes easily via its split and merge subnet functions, allowing you to split and merge subnets without losing any data.
You can import your existing IP allocation data via a CSV file upload. Alternatively, you can use an XML file created by Nmap to import addresses, or you can define the subnets yourself and have IPplan automatically fill in the DNS names for you. IPplan can import the DNS info via a zone transfer from your DNS servers.
You can set up multiple logins, so the entire network admin team has access to the IPplan database. You could even give the system administrators access to IPplan and require them to request IP addresses from you via the Web GUI.
IPplan is more than just an IP address tracking database. As you can see, you can also use IPplan to manage your DNS records, and IPplan implements "triggers" that allow you to run custom scripts based on actions taken in the Web interface.
If you're wondering why a browser can't find the Web server, you can fire up Tcpdump and see what's happening. Is the computer sending out DNS queries? Is it receiving a valid reply from the correct DNS server? By viewing the query and reply packets with Tcpdump, you can determine if the DNS server is replying with NXDomain for what should be a perfectly valid domain name or if the user changed the DNS server settings because he thinks that Google's DNS servers "must be faster" than your company's own servers. Or maybe the DNS queries and replies are fine, but the remote Web server is not responding. Then you would see the HTTP request packet leave the computer, but no replies from the Web server.
Tcpdump is a great tool by itself, but pair it with Wireshark, and you have an unbeatable system for troubleshooting network application issues. You can save your Tcpdump packet captures to files and open them in Wireshark for easier analysis. Wireshark gives you a GUI to examine Tcpdump captures and sort the data for more thorough analysis. You can compare time stamps on individual packets to see how long it's taking for a reply to be returned after a request has been made. And if you've synced the system clocks on client and server computers, you can see how long it takes for packets to travel between the two.
If you have a slow internal Web application, you can use Tcpdump and Wireshark to locate the bottleneck. If you see a long delay in the DNS lookup requests and replies but the actual HTTP requests and replies are fast, then you know the trouble lies with the DNS system or the network links to the DNS servers. If the DNS process is working normally, then you'll want to examine how long it takes for client requests to reach the server and how long it takes for the server to reply back. Wherever your network problem lies, Tcpdump and Wireshark can help you put your finger on it.
Books have been written about Tcpdump and Wireshark. Read them and learn all about these two utilities. You'll certainly improve your network troubleshooting game.
RANCID (Really Awesome New Cisco confIg Differ) is a versioning system for your switch and router configs. It uses either CVS or Subversion to store each new version of your configuration files. As it gathers and stores the configs for each of your devices, it runs a diff against the previous version to see what, if any, changes have been made. When it detects a change, it sends out an email with the details of that change to an address of your choosing. With RANCID, you'll know whenever a change has been made by your NOC team.
Because RANCID runs via a crontab entry, you can control how often it logs in and checks your configurations. If you are a stable shop and rarely make changes, you might have RANCID check once a day. If you are a more dynamic NOC and make changes frequently, you can set RANCID to check hourly or as often as is appropriate for your company.
One of the neat features of RANCID is that it includes a looking-glass server. You can take a quick peek at all the routes in your organization and search for any elements that are out of sorts when you suspect a routing problem on your network.
RANCID supports gear from most of the big networking vendors, including Cisco, HP ProCurve, Juniper, Foundry, and several others. It is known to work on Linux, BSDs, Mac OS X, and Solaris.
You can set thresholds that indicate when a device is busy or down and receive a notification via email, SMS, IM, and so on. Of course you can have separate logins for each of your NOC team, and you can set up an on-call schedule so that notifications go only to on-duty team members. OpenNMS also has an escalation handler, so if the level-one NOC techs don't take care of an issue right away, an engineer or manager can be notified to oversee issue resolution.
The Cacti graphing solution makes a good complement to OpenNMS. Although OpenNMS has the same graphing capabilities, Cacti's more intuitive Web UI allows nontechnical staff to build and manage collections of graphs that are interesting to them. For example, you could configure Cacti to graph data from your (SNMP-capable) HVAC controllers, and your facility maintenance team members could log in to Cacti and build custom views that display only the data they need to see. If one is watching fan rotation speed and another is tracking electrical power draw, they wouldn't have to view each other's data.
You can organize Cacti's graphs into trees, similar to the old Microsoft file system viewers used to display files in a directory structure. And with individual logins for each staff member, everyone gets their own view settings saved under their login.
MTR updates the statistics of the pings as it runs, so you can see which routers are slow to respond or which are dropping a significant number of ping requests. The results include the percentage of lost packets, the response times from each router (average, best, and worst), and the standard deviations for those times. How many times have you heard a user complaining "the Internet is slow," only to discover that the problem is a particular website or provider upstream from your office? MTR is a great way to see whether there really is a problem and to get a quick idea of where the problem resides.
One of MTR's more commonly used command-line options is -n, which stops MTR from doing reverse DNS lookups on the IP addresses of the routers it pings. This is handy when you're having DNS problems and don't want to wait for the lookups to timeout. Another useful option is -r, which issues a single summary report after running a certain number of pings (specified by the -c option) to each router. This can be used with scripts to build regular reports to be printed, emailed, or even inserted into a Web page.
This is by no means an exhaustive list of open source networking utilities available, and I've merely touched on their capabilities. Are there other free open source tools that you use regularly but we didn't list here? Leave a comment and let us know!
Dig
DNS problems plague us all, and they're easily overlooked when troubleshooting, so you need a reliable tool that provides detailed information about how users' DNS queries are being resolved. Why not use the tool made by the Internet Systems Consortium, the same group that produces the BIND DNS server software running the majority of DNS servers worldwide? That tool is Dig.At the heart of it, Dig is a command-line utility that performs DNS queries. That alone is helpful, but Dig can also tell you most everything about the queries and replies -- you'll sometimes need that extra information to determine why you're getting a strange reply from a DNS server. The default output of Dig provides you with all the data you'll require for troubleshooting: reply/error codes from the server, flags used in the query, a reiteration of your query, the answer to your query, how long the query took, which server it received the reply from, and how much data it received in the reply. Dig can be quite useful when you're trying to diagnose slow network applications, by determining how long it takes a computer to get DNS resolution for the application server's domain name.
Dig can ask for a typical name query, replying with an IP address when you give it a domain name. You can also do a reverse lookup: By using the -x switch and giving it an IP address, Dig it will return the corresponding domain name for that IP address. The -t switch lets you specify the type of query you're making, so you can ask for mail server records (MX), name server records (NS), text records (TXT), and more.
If you are sporadically getting incorrect replies to your DNS queries, it's possible that one of your DNS servers has a different set of DNS records than the others. With Dig, you can run the same query against each of your DNS servers to find out which one is providing the erroneous replies. Just give Dig the DNS server's address with the @ symbol in front:
dig @4.2.2.2 www.yourdomain.com
Are you troubleshooting DNS problems with servers that use transaction signatures? Dig lets you specify a TSIG key to use for your queries. Dig also lets you tailor IPv6-only queries to help you troubleshoot IPv6-specific problems.
Dig is a part of the client utilities of the BIND project. It is not generally installed by default, but is readily available on all Unix, Linux, and BSD variants, including Mac OS X. A Windows version is available too.
Nmap
Carrie Moss used it in "The Matrix Reloaded." Crackers, hackers, and network admins alike rely on it, and every networking consultant better have Nmap installed on his or her computer. Nmap is available for nearly every platform imaginable and is amazingly useful as a network and security analysis tool.Nmap is a lightweight security scanner that's heavy on utility. Nmap can perform tasks as simple as a ping sweep to see which IP addresses are active and responding, as well as carry off complex scripts to scan your systems for known vulnerabilities. Another fun feature of Nmap is the ability to analyze the reply packets it receives from a host to determine which OS the host is running.
Nmap is most commonly used to see which services or ports are open or available on a host. It supports both TCP and UDP scanning. You can give it a single host to scan or a CIDR (Classless Inter-Domain Routing) block or an entire list of hosts and networks from a file. A dizzying range of options allows you to specify which types of packets to send out and to see which hosts are susceptible to various remote attacks. Additionally, Nmap provides several options to bypass firewalls and other network filters that would otherwise block your scans.
Nmap also includes the Nmap Scripting Engine (NSE), which combines custom scripts with existing Nmap functionality to perform more specific discovery and attack analyses than Nmap does by itself. Fyodor and David Fifield gave an excellent talk and demonstration on the NSE at the Black Hat conference in Las Vegas last year. In the demonstration, Fyodor showed the results of Nmap scans against Microsoft company computers that used some of the NSE's MS RPC discovery scripts. The scripts used rpcinfo to gather info such as share names and usernames from the Windows computers. There are 177 NSE scripts available from Nmap.org as of this writing, and because they are user contributed, the list of NSE scripts is expanding at an amazing pace.
If you're a longtime user of Nmap but haven't kept up with Nmap news and releases, you'll want to check out the Zenmap GUI's new network topology feature, which lets you create an interactive network map based on information gathered by Nmap. The map begins with localhost at the center and displays all discovered hosts in concentric rings around it, the rings indicating the number of hops away the hosts are. From there you can shift the focus to another host or get more info by clicking a host's icon in the map. The shape of the icon refers to the type of device, and the size indicates the number of open ports.
All this makes Nmap perfect for checking on IP address usage, scanning for security vulnerabilities, and ensuring your firewalls and routers are operating properly.
KeePass
Oh the passwords! How many passwords do we have for all the various servers, switches, routers, and other network gear we have to manage? And when we have to change a password, we must be sure to notify all of the other people who have access to that equipment. A good password management system can save valuable time and spare you a lot of hassle.Enter KeePass, an encrypted database program to store all of your usernames, passwords, access URLs, and more. You can restrict access to the KeePass database with a password, a key file, or both. The password database is encrypted with either AES or the Twofish encryption algorithm, and not as one contiguous file but in 256-bit chunks -- decrypting a single piece of data nets a cracker little or no useful data. Plus KeePass encrypts all the data in its database, not just the passwords, so your usernames, URLs, and other notes are safe as well.
You can create groups for password records to help organize the info if you have a lot of passwords to track. Groups can have subgroups, subgroups can have subgroups, and so on. A search function helps you quickly find the password record you need.
How do you share the KeePass database with coworkers who are running Mac OS X or some other version of Unix? No problem. KeePass is ported to Windows, Mac OS X, various Linuxes, and popular mobile phone platforms, including iPhone, Android, and BlackBerry. Because the KeePass database is stored in a single file, it's easy to distribute among your NOC team. Did I mention that KeePass is portable, needing no installation on Windows or Mac OS X? You can carry it with you on a USB stick or download it to a computer without leaving any unwanted registry entries or library files.
Already using another password manager? KeePass can import your existing password database in formats from a variety of programs such as Password Keeper, CodeWalletPro, and Password Agent. Other file formats are supported through KeePass plug-ins.
IPplan
We network admins must keep track of which IP addresses we have, which are in use, and which are available to be allocated to the systems administrators who always want yet another IP address for their servers. Are you tracking your IP addresses in an Excel spreadsheet? Well, stop! Get the benefits of using a real database with IPplan.IPplan is not a generic spreadsheet or database application. It is tailored to tracking IP addresses, so it understands and enforces CIDR blocks. Each address record has support for contact info, hardware, DNS name, location, description, MAC address, NAT address tracking, and a generic "additional information" field. You can also upload a file to attach to the IP address record.
IP address records are organized into subnets (CIDR blocks), which are assigned to customers or autonomous systems. Subnets are further organized into network areas or ranges (supernets) within the customer hierarchy. Because IPplan is designed for use by ISPs, it works well for organizing enterprise addresses for companies with multiple locations and complex networks that use multiple AS (Autonomous System) numbers. If you decide to rework the subnets on your network, no problem. IPplan handles changes easily via its split and merge subnet functions, allowing you to split and merge subnets without losing any data.
You can import your existing IP allocation data via a CSV file upload. Alternatively, you can use an XML file created by Nmap to import addresses, or you can define the subnets yourself and have IPplan automatically fill in the DNS names for you. IPplan can import the DNS info via a zone transfer from your DNS servers.
You can set up multiple logins, so the entire network admin team has access to the IPplan database. You could even give the system administrators access to IPplan and require them to request IP addresses from you via the Web GUI.
IPplan is more than just an IP address tracking database. As you can see, you can also use IPplan to manage your DNS records, and IPplan implements "triggers" that allow you to run custom scripts based on actions taken in the Web interface.
Tcpdump and Wireshark
When things get really hairy and you can't figure out what's going wrong on your network, it's time to pull out Tcpdump. This utility lets you capture the network traffic on a network card and view the packets and frames in real time.If you're wondering why a browser can't find the Web server, you can fire up Tcpdump and see what's happening. Is the computer sending out DNS queries? Is it receiving a valid reply from the correct DNS server? By viewing the query and reply packets with Tcpdump, you can determine if the DNS server is replying with NXDomain for what should be a perfectly valid domain name or if the user changed the DNS server settings because he thinks that Google's DNS servers "must be faster" than your company's own servers. Or maybe the DNS queries and replies are fine, but the remote Web server is not responding. Then you would see the HTTP request packet leave the computer, but no replies from the Web server.
Tcpdump is a great tool by itself, but pair it with Wireshark, and you have an unbeatable system for troubleshooting network application issues. You can save your Tcpdump packet captures to files and open them in Wireshark for easier analysis. Wireshark gives you a GUI to examine Tcpdump captures and sort the data for more thorough analysis. You can compare time stamps on individual packets to see how long it's taking for a reply to be returned after a request has been made. And if you've synced the system clocks on client and server computers, you can see how long it takes for packets to travel between the two.
If you have a slow internal Web application, you can use Tcpdump and Wireshark to locate the bottleneck. If you see a long delay in the DNS lookup requests and replies but the actual HTTP requests and replies are fast, then you know the trouble lies with the DNS system or the network links to the DNS servers. If the DNS process is working normally, then you'll want to examine how long it takes for client requests to reach the server and how long it takes for the server to reply back. Wherever your network problem lies, Tcpdump and Wireshark can help you put your finger on it.
Books have been written about Tcpdump and Wireshark. Read them and learn all about these two utilities. You'll certainly improve your network troubleshooting game.
RANCID
We've all had that horrible sinking feeling in the pit of our stomachs when we've copied and pasted a new config into a router or switch and it stops responding. Did I remember to back up my old config before I uploaded the new one? How late will I be staying up tonight to fix this mess?RANCID (Really Awesome New Cisco confIg Differ) is a versioning system for your switch and router configs. It uses either CVS or Subversion to store each new version of your configuration files. As it gathers and stores the configs for each of your devices, it runs a diff against the previous version to see what, if any, changes have been made. When it detects a change, it sends out an email with the details of that change to an address of your choosing. With RANCID, you'll know whenever a change has been made by your NOC team.
Because RANCID runs via a crontab entry, you can control how often it logs in and checks your configurations. If you are a stable shop and rarely make changes, you might have RANCID check once a day. If you are a more dynamic NOC and make changes frequently, you can set RANCID to check hourly or as often as is appropriate for your company.
One of the neat features of RANCID is that it includes a looking-glass server. You can take a quick peek at all the routes in your organization and search for any elements that are out of sorts when you suspect a routing problem on your network.
RANCID supports gear from most of the big networking vendors, including Cisco, HP ProCurve, Juniper, Foundry, and several others. It is known to work on Linux, BSDs, Mac OS X, and Solaris.
OpenNMS and Cacti
OpenNMS has a place in every enterprise. It's a highly scalable network monitoring system that is completely open source software. A single server can monitor hundreds of thousands of network interfaces and produce nice graphs for metrics such as bandwidth usage, CPU, memory, and more.You can set thresholds that indicate when a device is busy or down and receive a notification via email, SMS, IM, and so on. Of course you can have separate logins for each of your NOC team, and you can set up an on-call schedule so that notifications go only to on-duty team members. OpenNMS also has an escalation handler, so if the level-one NOC techs don't take care of an issue right away, an engineer or manager can be notified to oversee issue resolution.
The Cacti graphing solution makes a good complement to OpenNMS. Although OpenNMS has the same graphing capabilities, Cacti's more intuitive Web UI allows nontechnical staff to build and manage collections of graphs that are interesting to them. For example, you could configure Cacti to graph data from your (SNMP-capable) HVAC controllers, and your facility maintenance team members could log in to Cacti and build custom views that display only the data they need to see. If one is watching fan rotation speed and another is tracking electrical power draw, they wouldn't have to view each other's data.
You can organize Cacti's graphs into trees, similar to the old Microsoft file system viewers used to display files in a directory structure. And with individual logins for each staff member, everyone gets their own view settings saved under their login.
My TraceRoute
My TraceRoute (MTR) is not quite as useful as it once was. MTR relies on ICMP packets to judge network latency -- and ICMP are the first packets modern routers will drop in favor of more important data traffic when they get too busy. However, I still find MTR a great tool for troubleshooting network links that traverse multiple routers. Specify a destination, and MTR shows you a list of routers that your traffic passes through on the way (as well as the destination itself) and the results of a continuous ping to those routers.MTR updates the statistics of the pings as it runs, so you can see which routers are slow to respond or which are dropping a significant number of ping requests. The results include the percentage of lost packets, the response times from each router (average, best, and worst), and the standard deviations for those times. How many times have you heard a user complaining "the Internet is slow," only to discover that the problem is a particular website or provider upstream from your office? MTR is a great way to see whether there really is a problem and to get a quick idea of where the problem resides.
One of MTR's more commonly used command-line options is -n, which stops MTR from doing reverse DNS lookups on the IP addresses of the routers it pings. This is handy when you're having DNS problems and don't want to wait for the lookups to timeout. Another useful option is -r, which issues a single summary report after running a certain number of pings (specified by the -c option) to each router. This can be used with scripts to build regular reports to be printed, emailed, or even inserted into a Web page.
PHP Weathermap
Sometimes you want the 10,000-foot overview of your network traffic. PHP Weathermap provides exactly that. It shows a logical map of your routers and the links between them, using different colors to indicate how busy each link is. PHP Weathermap is a good complement to an application such as Cacti or OpenNMS.PHP Weathermap does not handle its own data collection, so you'll need to pair it with another application such as Cacti, OpenNMS, MRTG, or RRDtool. PHP Weathermap has a plug-in that helps it integrate into Cacti, with some options available in the Cacti preference panels.
You will need to edit the map config files to adjust the appearance of your maps. You can do this by hand, though PHP Weathermap offers a GUI editor that runs within a Web browser. You can use the editor to create your nodes (routers and switches) and links, as well as produce a functioning map.
When you're ready for manual tweaking, you can add custom background images to the map and insert custom icons for your routers. You can also add subnodes, which allow you to display more information within the router's icon, such as CPU or memory usage. You can also insert parallel links or bonded links between routers.
Through further tweaking of config files, you can fine-tune the placement of router icons and the map's legend. If you have a more complicated map with plenty of router icons, you can create curved link lines between your router icons to help keep the map readable and less cluttered or cramped.
Top free open source tools for network admins: NtopNeed an sFlow or NetFlow collector to get a thorough look at your data traffic flows? Ntop will take NetFlow or sFlow data from popular switches and routers and display it in a Web GUI, complete with clickable links that take you to details about particular hosts or protocols or to actual conversations and flows.
There are interesting features to Ntop's output, such as identifying workstation users by their email addresses and (passively) detecting the operating systems of network hosts through packet analysis. Ntop will break down traffic volume on a per-protocol basis, helpful for comparing the traffic your network actually has to what you think it should have.
Ntop can give you a list of IP protocols, sortable by protocol type, as well as lists of traffic sources and destinations. Ntop also creates a matrix table of IP traffic, so you can see who is talking to whom and how much data is being passed between the two. Of course, data is not as useful if you cannot sort it. Ntop allows you to sort on both the traffic source and the destination.
Platforms supported include Windows and all major Unix types, such as Linux, the BSDs, Solaris, and Mac OS X. Although resource usage will vary by network size and the configuration options that you choose, Ntop should be very light on modern workstation and laptop hardware. Ntop's Web UI accepts multiple HTTP usernames and passwords, so each member of your NOC team can have individual access, and you can force Ntop to work with HTTPS.
Ntop supports a wide range of network protocol types, IP protocol types, and even network media types. There is support for several VoIP protocols, including Cisco SCCP, Asterisk's IAX protocol, and of course SIP. Ntop can even do protocol decodes on most common IP protocols. If you want the information for later retrieval and analysis, Ntop can record its network traffic data to RRD-style files on a disk.
By Unknown with No comments